
Monitor, analyze, detect, and respond to threats in real-time with an AI-driven Human-led service through open-architecture multi-tenant platform mAInGuard 24×7 protection of endpoints, servers, networks, identities, and cloud environments. Deploy unlimited incident response for immediate, complex, and modern cyber-attacks.

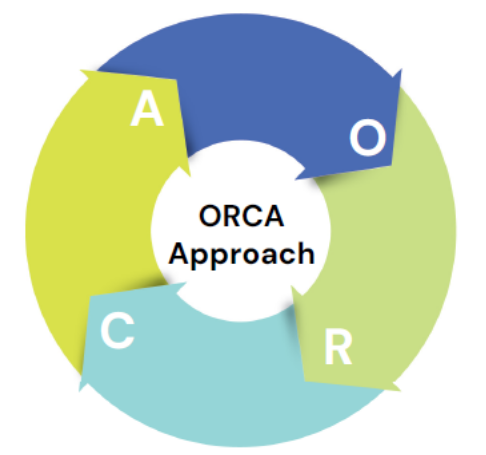
BSMART Managed Detection and Response (MDR) service platform is based on our ORCA (Observe, Response, Compliance, Awareness) philosophy. The ORCA philosophy is taken from the reallife world. Sharks only fear the killer whale or ORCA. BSMART unique platform acts as the ORCA to strike all the sharks in the cybersecurity ocean. Through our ORCA philosophy, our elite team of cybersecurity experts provides hands-on keyboard-based incident response and human-led threat hunting.
It is a machine-accelerated platform that uses modern-day technologies like Machine Learning and Artificial Intelligence for real-time threat hunting without taking away the human factor. Our cybersecurity experts use the platform to deliver hands-on keyboard-based threat hunting and incident responses. We don’t limit the number of Incident Responses (IR) in our MDR service. Hence, the customers don’t have to worry about retainers or hourly-based IR charges. Our MDR platform is based on open architecture, meaning it can easily integrate with any existing cybersecurity solution, eliminating the need for any additional investments.
Our MDR service covers the entire business ecosystem through our ORCA philosophy, whether hosted on the cloud or on-premise, by securing the endpoints, network, cloud environment, etc. The open architecture MDR easily integrates with any existing security solution to quickly align the detection and protection to the MITRE Att&ck Model and optimize response.
Our MDR also uses AI/ML for machine accelerated threat hunting, threat intelligence, contextual analysis, behavior analytics, and automated detection and responses. AI and ML ensure that our customers are not overwhelmed by false positives to save resources and time. It also helps in providing actionable insights so that even manual detection and response action can be done swiftly.
Collect, Store, Detect, Analyze and Visualize the Cyber Security Attack
Incident Investigation and Machine-Accelerated Automated Responses
Security controls to stay compliant with PCL-DSS, GDPR, HIPPA, NIST
Build Cyber Security Culture by raising the Awareness in the organization
At BSMART, we believe that risks can take shelter anywhere across the attack surface. Hence, a multi-signal, 360° is essential to protect your organization.
Through our MDR platform, we ingest data from various sources, including network, endpoint, cloud, switches, logs, events, etc., to strengthen our detection and response capabilities. As an open-architecture machine-accelerated platform, our MDR collects data from multiple sources, providing centralized visibility through a single platform.
Our SIEM administrators correlate Indicators of Compromise and detection data across the infrastructure, and our 24/7 SOC Analysts alongside our expert Threat Hunters analyze, investigate, and implement actions against the sophisticated threats that have bypassed your security.
Logs from the entire IT ecosystem which includes Storage, Databases, Web Servers, IOT Devices, etc.
Servers, Workstations, Endpoint Protection Solutions (EPP)
Firewall, Routers, Switches, Proxy, WLC Controllers etc.

Office 365, Google Workspace, IAM Solutions.

AWS, Azure, GCP, Cloud Workloads, Storage

Host and Network Vulnerabilities.
Whether you host your applications and business environment on the cloud or on-premises, we have the right tools and expertise to get the visibility to see the security gaps that other MDR providers might miss.

Disparate third-party data sets are converted into actionable threat intelligence to identify malicious actors lurking on your network.

Our Cyber Security experts spend a considerable amount of time understanding adversary tactics, techniques and procedures by analyzing indicators of compromise, to give you the benefit of ‘smart defense’ driven by adversarial intelligence.

The use of the latest threat detection technologies enables retrospective threat hunting that helps search for threats by going through rich meta data and retrospective analysis.

Tailored data science algorithms, ML and statistical data is merged and analyzed to identify potential risks that cannot be detected through conventional security products.

Superior telemetry integrated with high-fidelity threat intelligence hunts for threats across endpoints that have evaded security protocols.

Our global SOCs enable our cybersecurity experts to work round-the-clock for continuous threat hunting.

Cyber adversaries don’t have any working hours. Our cybersecurity experts work 24/7 so that cybercriminals cannot take advantage of non-working hours to penetrate your system.
Built with open architecture, BSMART MDR platform can integrate with your existing security solutions to enable you to leverage existing technologies and eliminate reinvestments.

Our machine-accelerated MDR platform is used by our cybersecurity experts to deliver human led, keyboard-based threat responses.

BSMART MDR platform has built-in SIEM capabilities that allow retaining unlimited logs to help you abide by primary compliances and you don’t have to worry

Our cybersecurity experts conduct thorough vulnerability assessments and penetration testings to identify potential loopholes and mitigate them.

We match your security posture against the CIS baseline security to detect deviations. Our cybersecurity experts also provide our customers with a detailed report and help them align with the benchmark security.